The Serverless Journey: From Developer Success to a Cloud Center of Excellence
Enabling Serverless in the Enterprise

Though the volume of serverless talks is lower this week, the quality and impact lacked nothing. Two must-see presentations emerged highlighting important practices for succeeding with serverless in the enterprise. Jessica Feng (Serverless Business Development at AWS) and David Anderson (Director of Technology at Liberty Mutual) outlined key steps for scaling success across an organization, and Ajay Nair (Director of AWS Lambda at AWS) included great security considerations as he highlighted the business value of serverless.
In this post I tease out common threads that every enterprise I work with is wading through on their serverless journeys.
- Outcomes: serverless has a track record of delivering customer and business benefits.
- Adoption: serverless adoption in the enterprise is a journey that scaled development success in a consistent and secure way.
- Security: modern app development yields modern security best practices for enterprises.
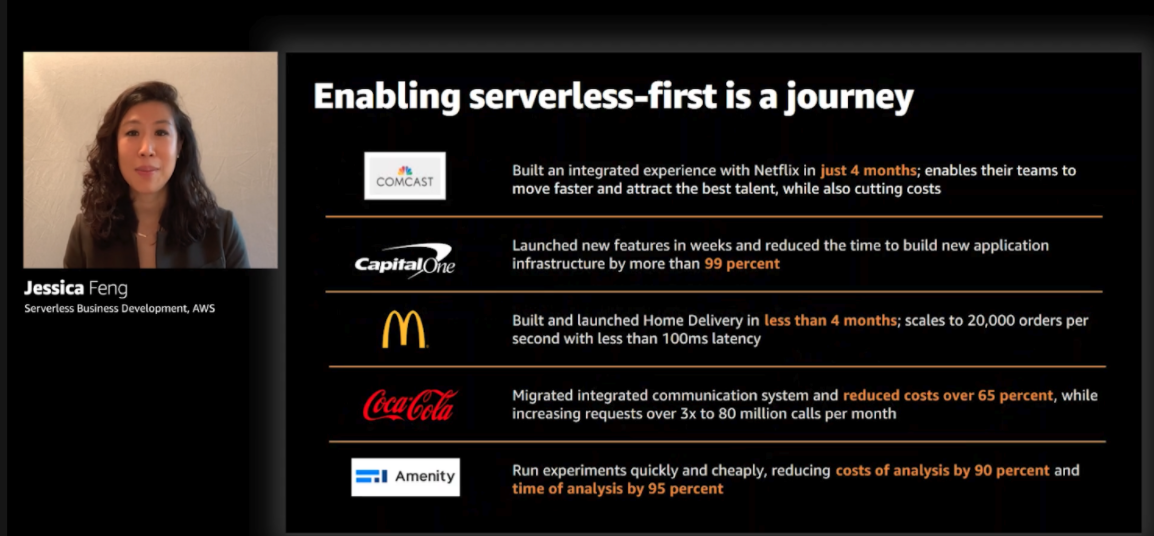
Serverless has a track record of delivering customer and business benefits.
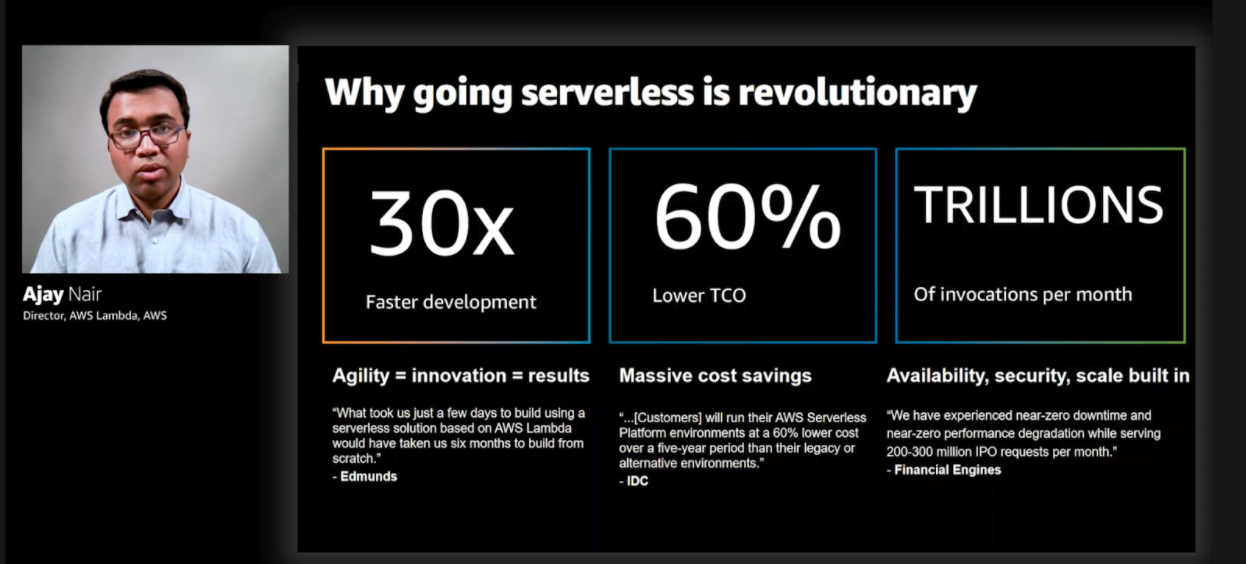
Serverless just celebrated its 6th birthday, and now has enough of a proven track record for delivering results that adoption is becoming more pervasive, even in historically traditional enterprises. What’s most compelling is how the value of serverless delivers results that seem at odds: faster speed & lower costs AND better scale, quality & security.
Once emerging technology proves that it helps deliver such clear benefits (especially when they are at opposite ends of the speed←→reliability spectrum) history shows that proliferation in the enterprise comes next. You need not look further than how virtualization, and more recently containers, took off in the enterprise. Both technologies increase agility and improve quality.
So, what does the next wave of serverless adoption look like, then, for enterprises?
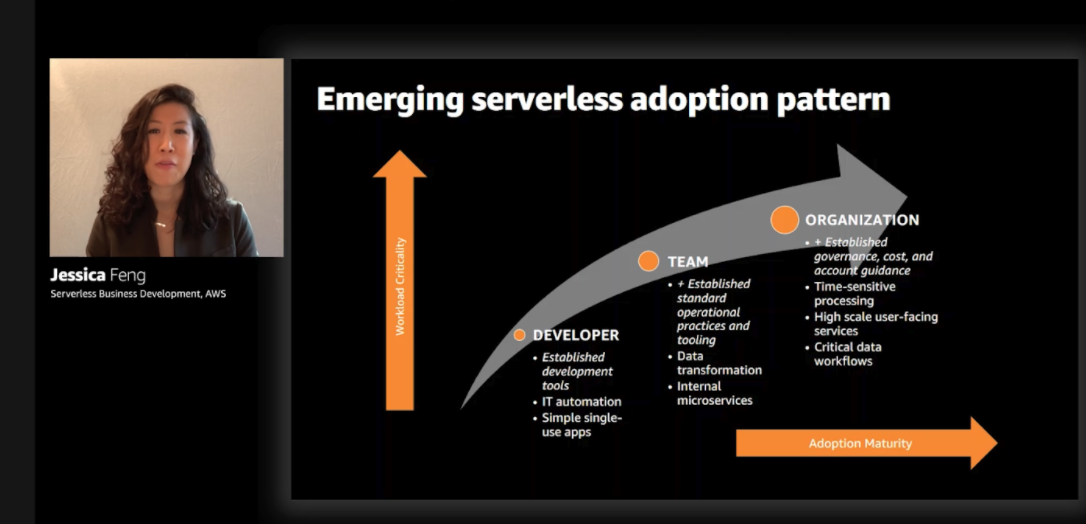
Adoption in the enterprise is a journey that scales development success in a consistent and secure way
Jessica Feng and David Anderson articulated this well in their session.
Jessica highlighted how AWS saw many of their customers resolve the friction of developer experience and security "by working hard to define a paved path where there's development teams and reduce the amount of time to get code from idea to production and successful examples of this includes aligning existing processes skill sets and culture with patterns of automation integration, continuous delivery and monitoring service architectures."
She also included a visualization of what the journey looks like for successfully scaling initial development success, more pervasively across the organization.
David went on to dive into specific details of how he and the team progressed on this journey at Liberty Mutual. One of the lines that really resonated with what I see in our customer base is the focus on scaling success by understanding how security and governance fits into the journey.
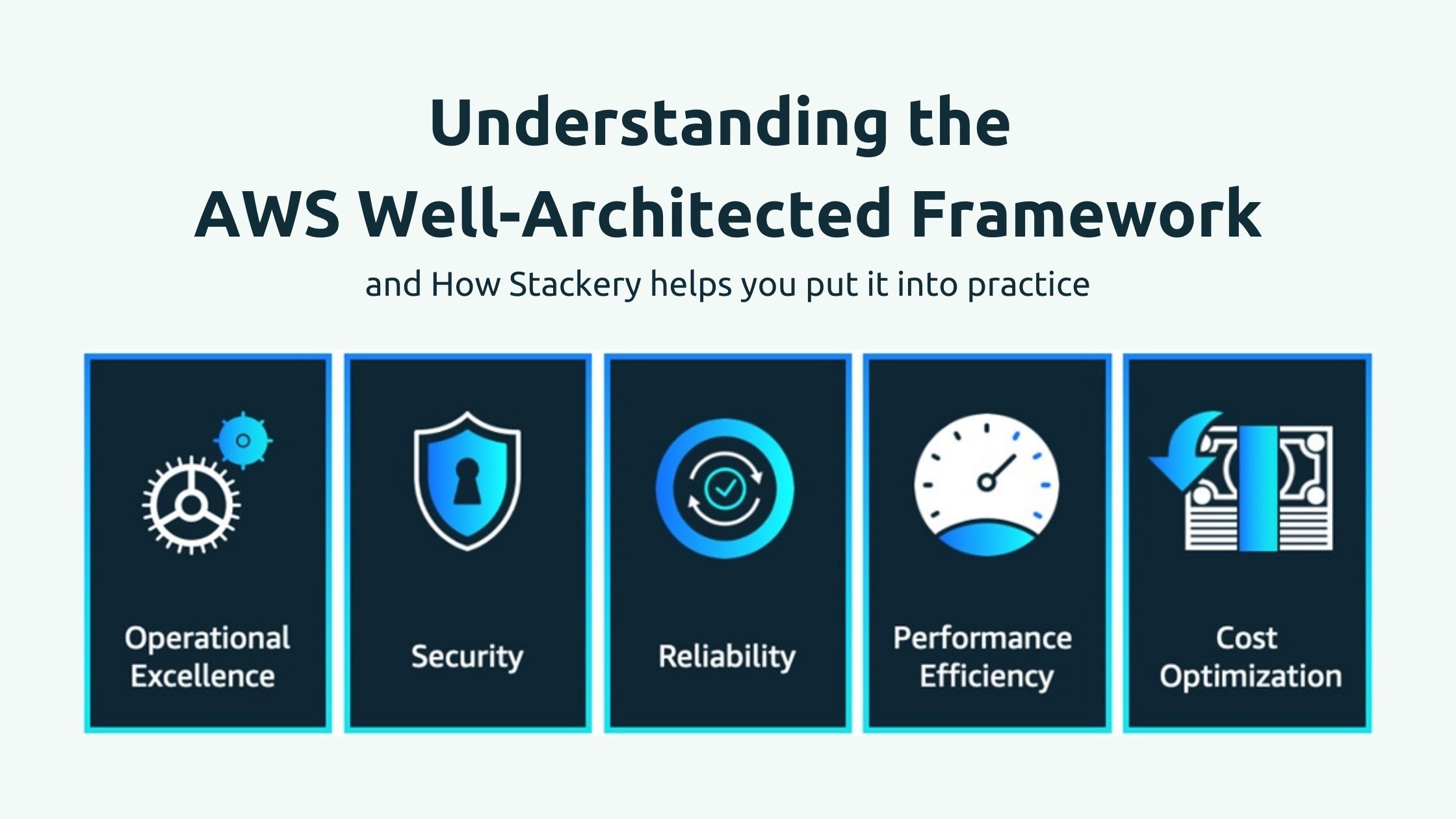
He said, "Over the past 12 months is really starting to scale, we find that word 'protected' has been a game changer. I believe this is the secret sauce of cloud adoption, the five pillars [of the Well-Architected Framework] have been very effective in driving the right conversations in our teams operational excellence, security, reliability, performance efficiency, cost optimization."
So, then, how is security different or better with serverless?
Modern app development yields modern security best practices for enterprises.
Whether you're looking for ephemeral, moving-target security practices, or ensuring least privileged access for serverless resources, serverless helps companies enforce their modern security posture.
Ajay outlines this well. He started by saying, "No modern application can truly drive customer value without nailing a security proposition."
From there he articulated three key security-related capabilities. First, how with the Lambda compute substrate, the compute is ephemeral—meaning it only spins up as needed and has a very finite lifetime.
Second, how Lambda "isolates each individual request from each other by guaranteeing an isolated set of resources for every request that your service handles, which also gives you consistent performance benefits".
And third, he talked about how serverless helps avoid binding to a machine or executable, saying that with Lambda "it's not like you're binding your work to a machine or a collection of machines or a specific collection of chips, but instead allow you to focus on matching compute resources, memory, CPU, and network to code and executable."
It's these sorts of security practices that, when applied consistently and at scale, allows centralized IT teams to fuel a chain reaction: empowering their developers—which thereby empowers their customers, partners, and employees with modern application experiences.
Related posts
And how Stackery can help you put it into practice