Analyze and audit your infrastructure as code with stack.new

Defining and managing your AWS resources using an Infrastructure-as-Code (IaC) approach implemented with CloudFormation templates makes a lot of sense. While implementing IaC is a widely accepted best practice, it does come with challenges. Managing your infrastructure from lines of code and text-file templates, in the case of AWS CloudFormation, can quickly become overwhelming. We built stack.new to ease that pain.
Stack.new is publicly available and free. It provides an automated way to visualize your infrastructure code, along with performing built-in checks to make sure your CloudFormation template follows best practices. All you need to do is drop in the link to one of your CloudFormation templates and stack.new will return a visualization and audit of your code. You can toggle from visualization to code view at any time and add or modify resources. The audit will identify issues, including those related to weakly-scoped IAM permissions, with links to related learning materials to help you solve them.
Don’t worry, if you’re not familiar with IaC. Later in the article, we provide an overview of IaC, along with a deeper dive into its benefits and potential issues.
But first, let’s take a look at an example of what stack.new can do with a CloudFormation template.
Visualize CloudFormation templates
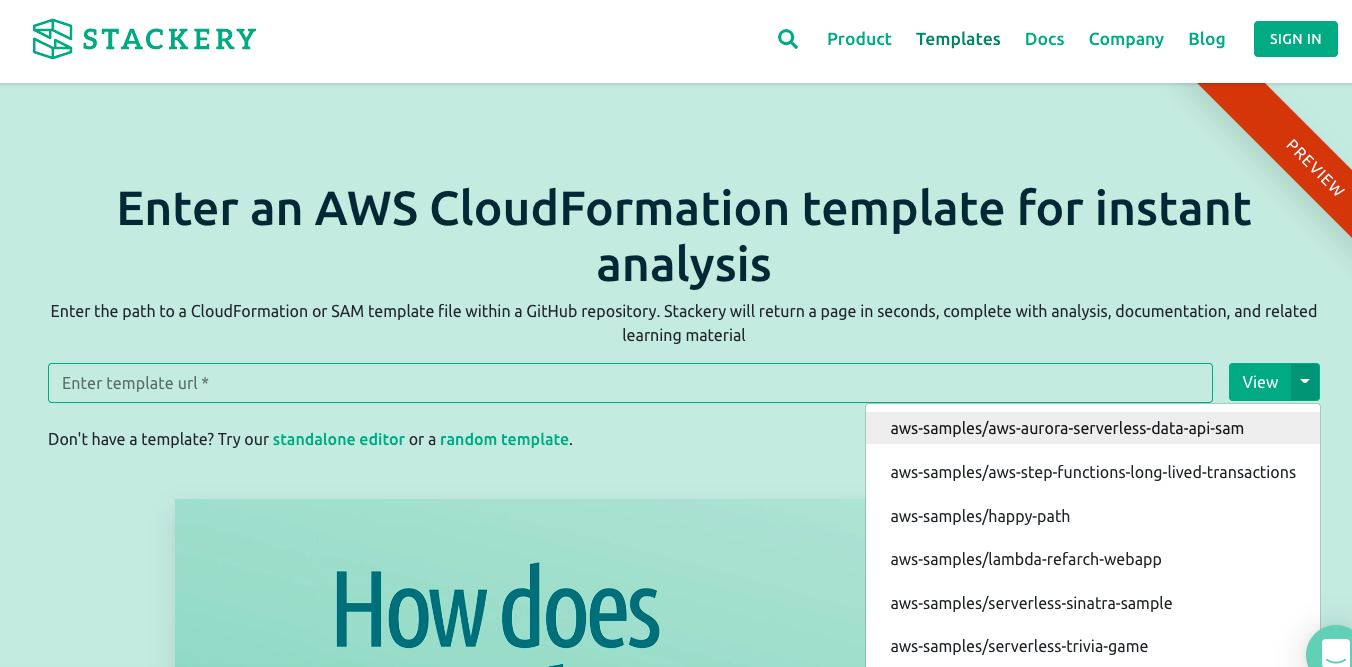
On the stack.new page, paste in the GitHub URL to a publicly accessible CloudFormation template, written in YAML. Stack.new then uses Stackery Design Canvas to instantly produce a visualization of your AWS infrastructure. If you want to see how things work first, we have several templates you can try out. In the screenshot below, you can see some of the templates you can choose in the View button’s dropdown list.
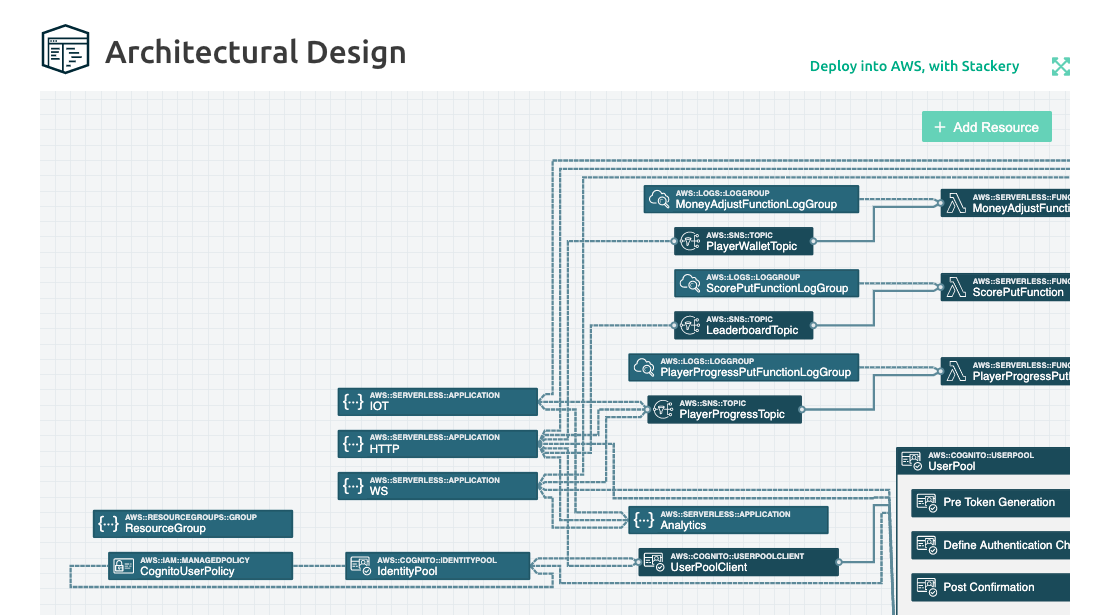
For this example, we chose the serverless trivia game CloudFormation template. After selecting it from the dropdown, the following IaC visualization is automatically generated:
Diagramming your architecture in this way allows you to quickly understand the relationships between your resources and can become an indispensable planning tool. While you can access and directly edit your code at any time, the days of having to dig through it line-by-line to get a handle on things are over.
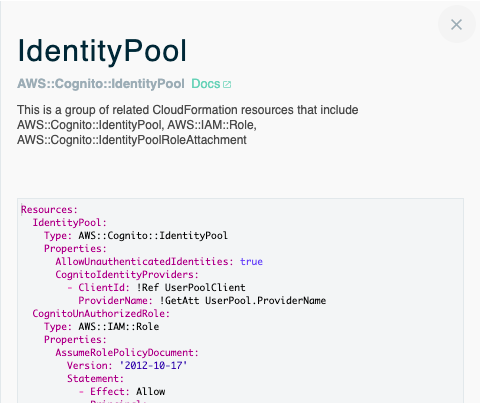
While a visual diagram of your template alone can provide a lot of value, you can do much more with stack.new. For example, you can double-click on a resource to see its configuration and what other resources are grouped with it. Here are the resources grouped under IdentityPool in the serverless trivia game template we chose above:
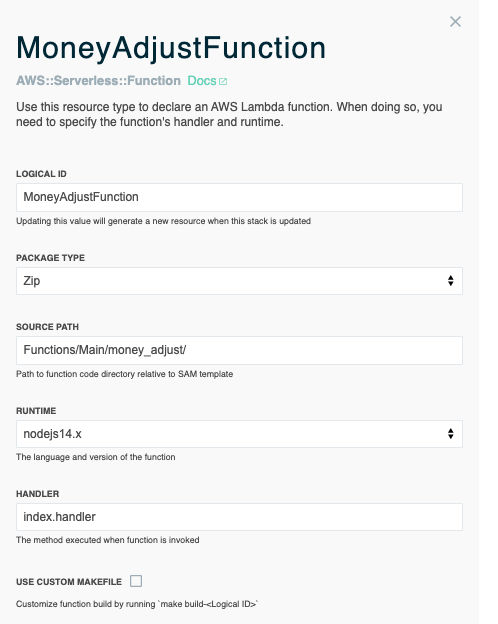
Some resources include the option to be modified directly from the visualization. For example, the MoneyAdjustFunction resource, in the serverless trivia game template, has a dropdown menu and checkbox options.
Caption: The MoneyAdjustFunction resource, in the aws-samples/serverless-trivia-game template, can be modified in the visualization
You can also add new resources to your template by dragging-and-dropping them onto your canvas. Just click the “+ Add Resource button” to get a menu of possible resources you can add.
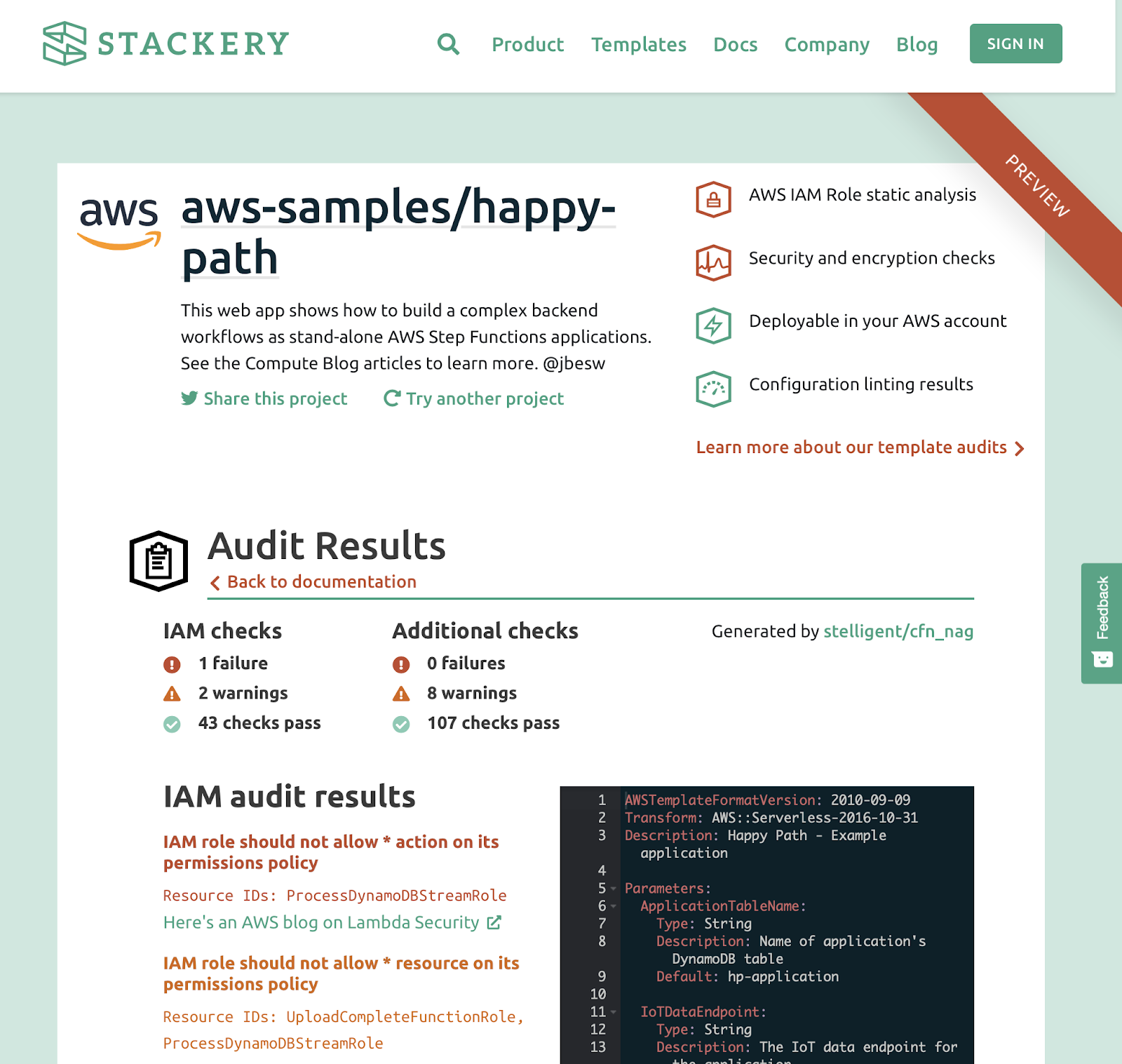
Audit IAM roles
Stack.new also performs an audit to validate CloudFormation templates, checking to see how well they hold up against best practices. One important assessment stack.new performs concerns IAM roles. Stack.new evaluates what actions each resource can take with other resources to ensure IAM roles are tightly scoped and don’t have overly broad permissions.
Stack.new identifies the problematic code and provides links to resources to help you solve each issue.
We’ve been pleased to hear from several developers who are already using stack.new to not only uncover issues, but to also iteratively test and refine their code until problem areas are knocked out.
How do they do it? After stack.new hones in on an issue, the developers research a new approach and run the template again. If the issue is still there or new ones pop up after the change, they continue this process until everything passes the stack.new audit.
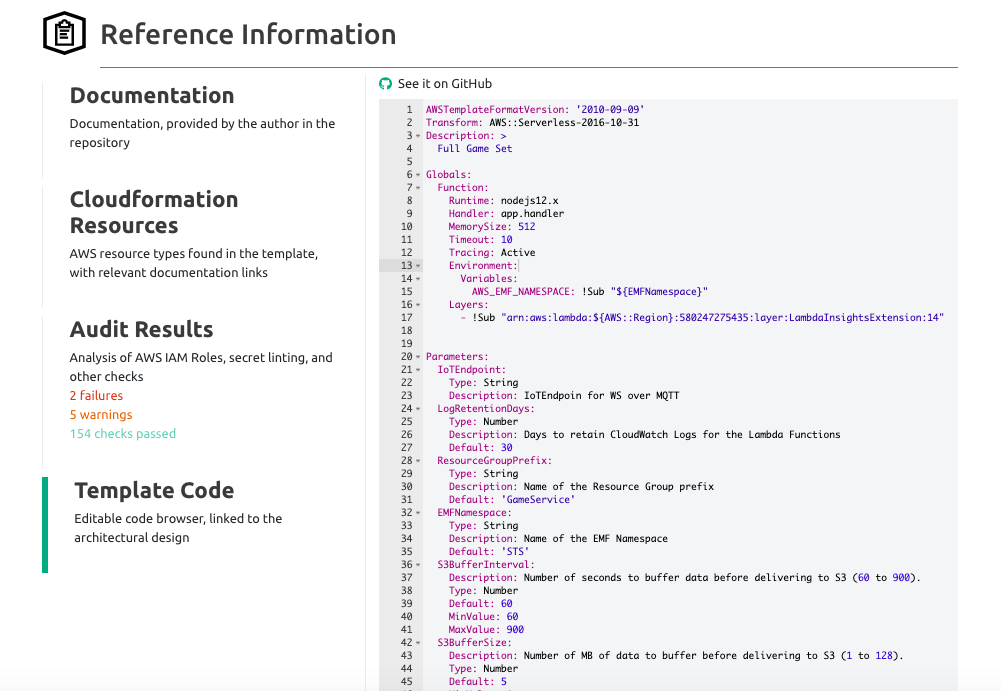
As you work to get to the bottom of things, you can always view and directly edit the code by using the Template Code area of stack.new’s Reference Information section.
Perform security and encryption checks
In addition to the security checks related to IAM roles, stack.new also runs encryption checks. In the following screenshot, the report identifies a missing KMS key which is used to manage encryption configured within CloudFormation templates.
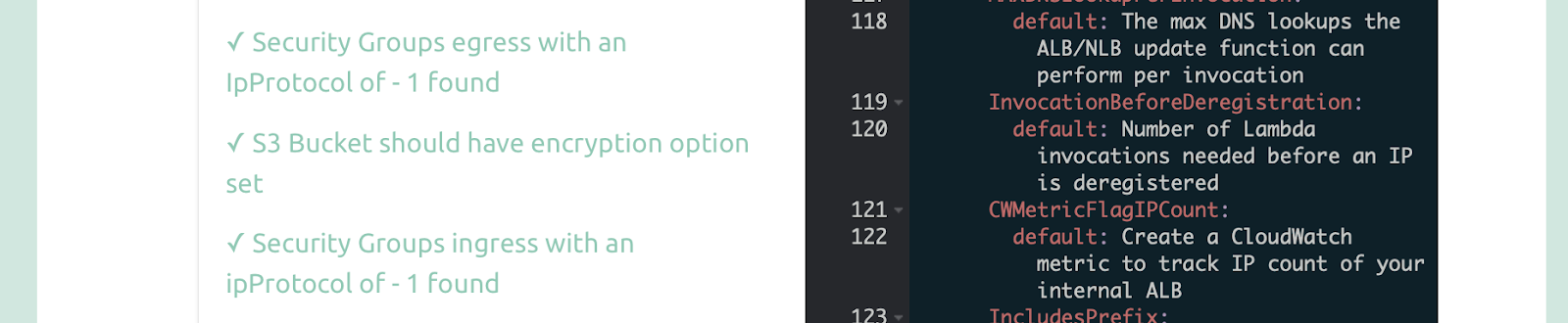
Stack.new also checks encryption configuration for relevant resources like S3, EFS and others. In the example below, the audit reveals that the S3 bucket should have an encryption option set.
Understanding Infrastructure as Code
We’ve focused on how visualization, audits and resources provided by stack.new can help you gain a better understanding of and improve Infrastructure-as-Code CloudFormation templates. Now, let’s take a closer look at what IaC actually is, along with some of its benefits and drawbacks.
It turns out the name, Infrastructure as Code, is very explanatory. With IaC, you use code to define your infrastructure and the resources needed. AWS CloudFormation calls for IaC code to be written in YAML or JSON and delivered in text-file templates.
Defining your infrastructure with code allows the provisioning process to be automated. It also enables the consistent creation and maintenance of many infrastructure environments. Setting up your entire infrastructure now comes down to executing a script (or executing an API call in the case of CloudFormation).
IaC removes the process of manually building your infrastructure and provisioning resources using the AWS management console or CLI. This speeds things up, while reducing human error, risk and costs. It also makes keeping a wiki up to date unnecessary. Everything is automatically documented in the code. This means you can implement versioning and more easily track infrastructure changes. You’ll have an always current, step-by-step blueprint outlining how to set up your infrastructure. Using IaC templates also makes it much easier to start the process of building similar infrastructures in new environments or geographical regions. Planning, deploying and scaling applications becomes simpler and easier to manage with IaC.
IaC templates democratize infrastructure knowledge across the organization, along with providing a convenient way to review and consistently implement policies. For example, ensuring that an organization’s IAM policies are consistently applied would be much easier by including approved code in all relevant IaC templates. IaC gets everyone on the same page, reducing the risk associated with only a few experts having a full understanding of the company’s infrastructure. What if those experts leave? With IaC, the instructions are left behind. This also helps new employees get up to speed fast. And the increased visibility brings teams that otherwise might have been siloed closer together. Developers, operations and IT can now more efficiently work together, using code as their common language. Those teams can boost the quality of their IaC even further by using a git-based peer-review process, with a repository like GitHub, BitBucket, GitLab or AWS CodeCommit.
While planning and managing your infrastructure with code is clearly a better option than the manual approach, IaC comes with some of its own complexity. As your infrastructure grows, so will the lines of code written to define it and the templates created to manage it. This can present an information management challenge. It can also be difficult to know if the code written meets best practice standards or will deploy correctly. And, in the case of CloudFormation, there’s a lot to learn and its templates can be hard to follow. We built stack.new so you can enjoy IaC’s benefits and successfully use it with CloudFormation, while avoiding these shortcomings.
How Stack.new can help
Within seconds of providing a link to your IaC-based CloudFormation template, Stack.new will generate a visualization, perform an audit against best practices and provide related materials that can help you solve any identified issues.
CloudFormation IaC is very nuanced, with a lot to learn. You and your team can make sense of complex code and get on the same page much faster with stack.new visualizations of your CloudFormation templates. You can add and remove resources using Stackery’s drag-and-drop Design Canvas then see how the code was modified with a single click. This is a great way to learn IaC, the ins-and-outs of CloudFormation and to rapidly level up skills. Once you have a Stackery account, these visualizations can serve as the go-to documentation and source of truth for your team.
Stack.new also helps improve your IaC by conducting an analysis of your AWS CloudFormation template to see how well it compares to best practices, including several from the AWS Well-Architected Framework. Stackery uses tools like Stelligent's cfn_nag and AWS CloudFormation Guard, in combination with custom logic, to check against numerous rules. It then provides an audit report with identified issues, along with links to recommended learning resources to help solve them. It’s a fast and painless way to audit CloudFormation templates.
In a perfect world, everyone on the team would be up to speed on IaC best practices and organizational policies and would always write flawless code reflecting both. But the real world is messy. Familiarity with particular tools is sure to vary and it's hard to onboard newcomers to a large codebase of YAML. Stackery's bidirectional code editor and infrastructure visualizer, reinforced by audits, helps balance the needs of broad team understanding and onboarding with the versioning, peer-review, and repeatability strengths of Infrastructure as Code. In fact, we’ve seen many customers onboard their whole team exclusively through Stackery’s visual editor, learning the details of CloudFormation IaC only after they’ve had hands-on practice with particular AWS infrastructure resources.
What’s next for stack.new?
We’re just getting started with stack.new. Here are some of the things we’re working on:
- Adding as many automated checks as possible to the CloudFormation template auditing process.
- Making it easier to rapidly iterate on a given template, so you can audit, learn, and improve it faster.
- Building out the collection of sample templates, so there will be something in place to get you started in just about any situation.
- Adding a report to let you know if the template you submit could be deployed successfully and how long it would take. We also hope to provide information about the necessary parameter data needed for successful deployment, along with information by region. For example, if an AWS region lacks the features the template being tested needs to function it would be flagged.
The bottom line? We want to make stack.new as helpful as possible to your IaC CloudFormation development process. So please give it a try and let us know your ideas to make it even better.
Try out stack.new with your own template or one of ours to see sample visualizations and audits.
Related posts


Truly composable and maintainable CloudFormation is now within reach